In a world where security and personal data protection are becoming increasingly more important, many organizations no longer want to rely on just one single login action for securing access to web applications. To increase the chance that a genuine user can be safely identified during a login process, web applications now use multi-factor authentication (MFA), often implemented as two-factor authentication (2FA) by asking the user to provide two proofs of identity.
In addition to SMS-based 2FA, Uptrends also supports setting up 2FA that would require normal users to fill in a code they get from a mobile application. This approach is known as Time-based One-Time Password (TOTP, or OTP) multi-factor authentication.
Such one-time passwords are typically valid for a short period of time (usually 30 seconds), and must be entered as part of the authentication procedure in the web application. These codes are algorithmically generated based on the current timestamp and a secret: a value known to both the authenticator app and web application, meaning they will calculate the same values. That way, if the value entered by the user matches the value expected by the web application, it can verify that the user has access to the same secret value, and should be allowed to access the application as well.
Regular flow of an OTP-based 2FA scenario
The flow we expect to see during the two-factor authentication procedure via mobile application-based one-time password in a web application is as follows:
- After navigating to the login page of the application, a user types their login credentials into the text fields of the login page. This part is the first identification step of 2FA.
- After the login credentials have been entered, the web application typically navigates to a new page containing a single text field, where the one-time password should be entered.
- The user opens their respective authenticator mobile application, which should list a (usually 6-digit) code, along with an expiration counter.
- The user enters this code into the web application, and can proceed with logging in (provided the code matches with what the web application expected, and hasn’t expired yet).
Overview of the Uptrends solution for OTP-based 2FA
Since the OTP codes are generated by an algorithm, the only requirement for being able to calculate them is knowledge of the secret. By adding this secret value to your account vault, we can calculate the correct value, and it can then be used in the same way you would use a username or password from the vault.
Unlike SMS-based 2FA, you can configure OTP-based 2FA yourself. Do keep in mind that you will need access to the secret - it may be listed in the 2FA configuration on your end, or your administrators may be able to tell you. If your organisation makes use of QR codes to register the OTP in mobile apps, the secret may be obtained from those as well. If you need any assistance, feel free to contact our Support team.
Steps for setting up OTP-based 2FA in a transaction
- In addition to the regular login credentials (which you can store in and use from the vault), you’ll need to know the secret for your OTP-implementation. The secret will typically be an alphanumeric code which you should be able to find in your OTP configuration. Alternatively, if your organisation uses QR codes to configure the mobile authenticator apps, the secret can be retrieved from those as well (scanning the code will lead to a URL that contains the secret).
- Once you know the secret, you have to add it to the vault. In an appropriate vault section, create a vault item of type One-time password configuration.
- Give the vault item an appropriate name (and, optionally, a description), and fill in the Secret. If necessary, you can edit the hashing algorithm, number of digits, or expiry time for the generated OTP-codes, but the defaults should be the correct values in most cases.
- Save the vault item.
- Now, the OTP configuration is available for use in your transaction scripts, in the same way you’d use for any credentials or files stored in the vault.
- At the correct place in the transaction script, add a Set action.
- Add the right CSS or XPath selector to point to the text field waiting for the OTP-code on the page.
- For its value, click the icon, and select One-time password.
- Select the correct OTP-configuration from your vault, and click to use the OTP-configuration for this action.
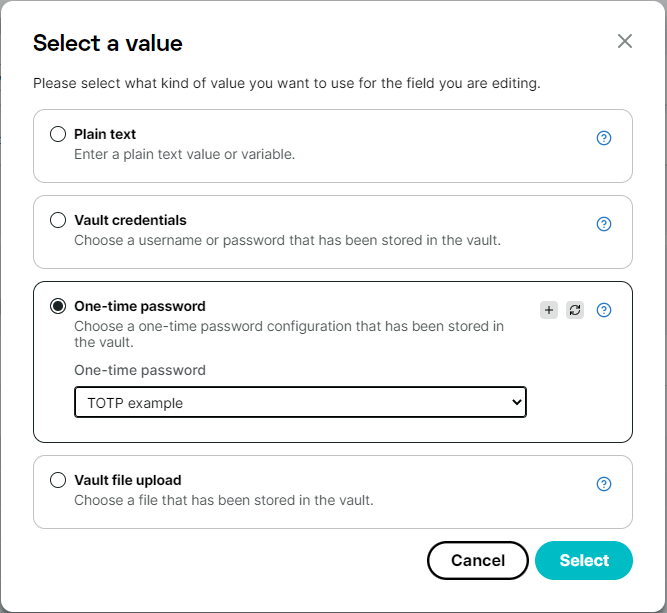
- The transaction is now configured to generate the correct OTP-code and enter it into the text field. From here, you can proceed with the transaction as normal.
Cost
There is no additional cost associated with an OTP-based 2FA setup in your transaction. The regular cost of a transaction applies.